It’s no secret that cybersecurity experts are more in demand than ever, but if your options are hiring in-house or outsourcing, what’s the better approach?
By definition, cybersecurity is what we call the practice of protecting any system, software, or data connected to the internet from unauthorized access, attacks, or threats linked to hacking, phishing, malware, and ransomware attacks. The aim of the game is to ensure the confidentiality, integrity, and availability of sensitive information and systems, and to minimize any potential damage from security breaches.
While this seems relatively straightforward, hiring a cybersecurity specialist is not. New data sourced from Checkpoint found that when compared to the same period last year, global cyberattacks increased by 38%, with the United States alone seeing a surge of 57%.
Given the complex nature of cybersecurity, many organizations are scrambling to find the right person to protect their digital assets – they know it needs to be addressed, but aren’t quite sure how to proceed. If this is something that resonates and sounds all too familiar at your organization, then the first step is working out whether to outsource or hire in-house.

What is the role of cybersecurity in an organization?
While most of us appear to grasp the importance of cybersecurity in a commercial enterprise, much fewer are able to identify what a day in the life of a cybersecurity specialist actually looks like.
In its simplest form, the field of cybersecurity involves the protection of systems, networks, and sensitive information from unauthorized access, theft, or damage. Although the concept still applies to individuals, companies around the world are rightfully prioritizing cybersecurity in the wake of a growing number of incidents, threats, and attacks.
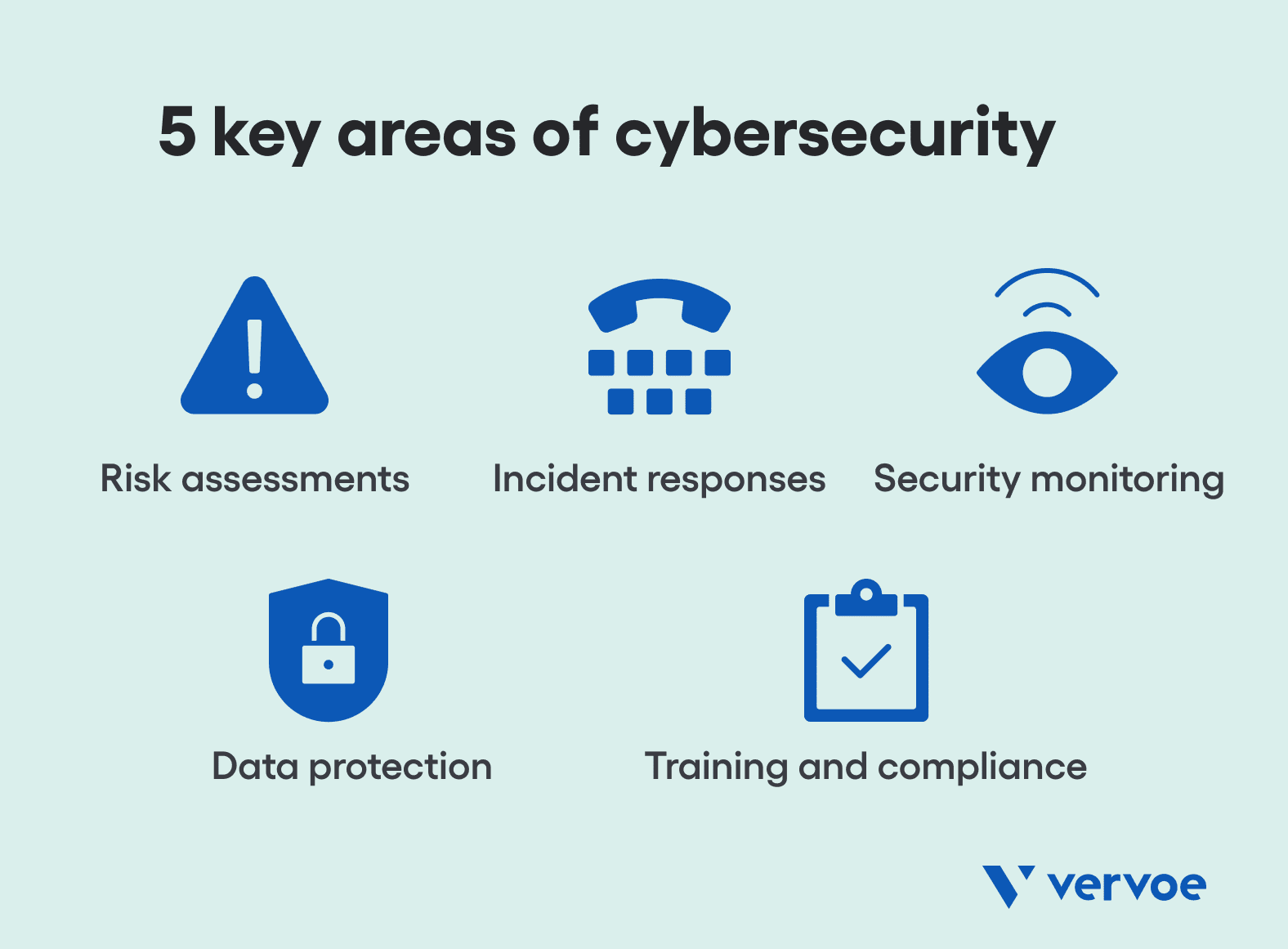
In commercial agreements, cybersecurity experts are responsible for identifying and mitigating potential security risks, responding to security incidents, and implementing measures to prevent future incidents from occurring. Other key areas of responsibility include:
1. Risk assessments
A cybersecurity specialist will regularly run reports to identify information assets that could be affected by a cyber attack, such as hardware, systems, laptops, customer data, and intellectual property. Risk assessments are crucial for evaluating the organization’s current security levels and identifying potential security risks, such as vulnerabilities in systems or processes.
2. Incident responses
Incident response is a term used to describe the process by which an organization handles a data breach or cyberattack, including the way the organization attempts to manage the consequences of the attack or breach. Cybersecurity experts are not just responsible for preventing any digital threats but are also key to ensuring the wider team knows what to do next in the event of a cyber attack.
3. Security monitoring
Like it or not, cybersecurity is not a field that can be approached with a “set and forget” mindset. As technology rapidly evolves, so too does the nature of a breach, threat, or attack. Cybersecurity experts are required to gather and analyze information about new and emerging threats to the organization, and continuously monitor systems and networks for security incidents and anomalies.
4. Data protection
A key responsibility of any cybersecurity specialist is to ensure that sensitive data is protected and stored securely, in addition to implementing measures to prevent potential data loss or theft. This will often include tailored access control measures designed to ensure that only authorized individuals have access to sensitive information and systems.
5. Training and compliance
Employees often are trained by a cybersecurity specialist on best practices to protect the organization. While this may seem like common sense, staff training is one component of ensuring that the organization is in compliance with relevant security standards, such as the Payment Card Industry Data Security Standard (PCI DSS) or the General Data Protection Regulation (GDPR).
Why cybersecurity experts are needed more than ever in 2023
Cybercrime has been increasingly dominating the headlines in recent years, and no organization or industry is immune from a potential breach. On average, it takes 197 days to discover and 69 days to contain a cybercrime incident, but the true cost of cyber attacks, such as lawsuits, insurance rate hikes, criminal investigations, and bad press, can easily inflict irreparable damage to a company, and take years to recover from.
According to the “State of Cybersecurity Resilience 2021” report from Accenture, the cost of data breaches will rise from around $3 trillion dollars each year to more than $5 trillion dollars in 2024. Thankfully, one of the key strategies to combat potential threats, protect digital assets, and avoid becoming another statistic is to enlist the help of a qualified cybersecurity specialist.
Unfortunately, this is usually the first pain point. Hiring a cybersecurity expert isn’t easy, especially if you aren’t particularly skilled in this field yourself. It can be difficult to separate top-tier talent from those who simply claim to be, especially when we’re facing a cybersecurity skills shortage around the world.
Although 464,000 in-house cybersecurity jobs have been filled in the past year, the cybersecurity talent gap has grown twice as much as the workforce, increasing 26.2% year on year. As such, it should come as no surprise that many companies think that the solution to this burgeoning labor crisis is to outsource – but is that really the case?

Should companies outsource cybersecurity or hire in-house?
Once upon a time, the concept of outsourcing parts of your business operations would be met with looks of shock and horror. The concept was immediately associated with offshore call centers, or third parties who simply didn’t know – or care – about the business that they were representing or working with.
Today, it’s an entirely different story. Post-COVID-19, many businesses were forced to consider new solutions for old problems, such as labor shortages or access to the right types of industry experts who may not live in your city.
While the digital revolution has made outsourcing easier than ever before, it’s not a case of can cybersecurity be outsourced, but rather should cybersecurity be outsourced? Furthermore, is it safe to outsource IT security? While these are all valid topics that should be explored before making a decision on the best option for your organization, the reality is that there’s no one size fits all solution.
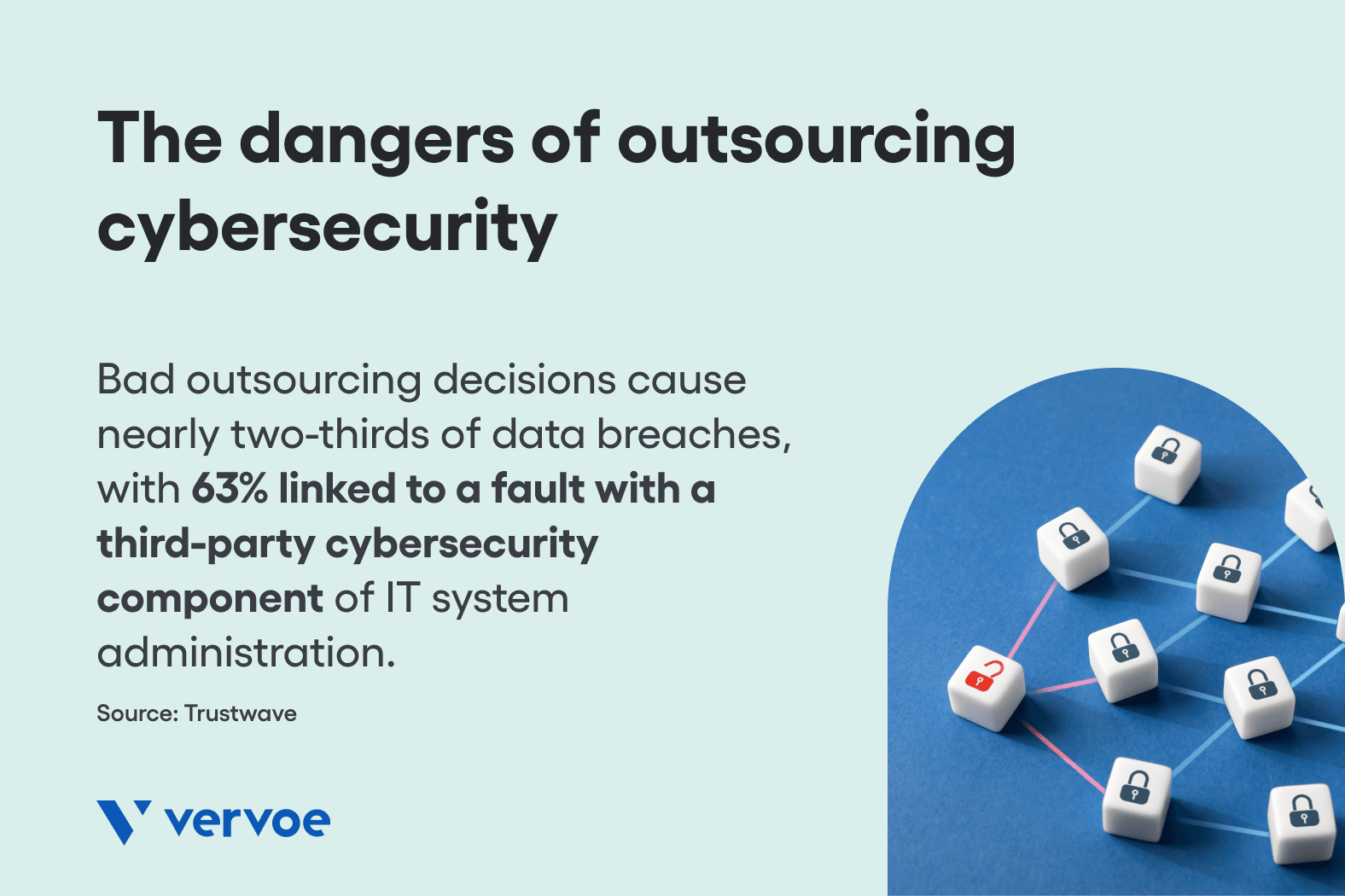
Despite the belief that the choice to outsource cybersecurity is easier and cheaper, what’s the true cost? Bad outsourcing decisions cause nearly two-thirds of data breaches investigated by security firm Trustwave in the past year, with 63% linked to a fault with a third-party cybersecurity component of IT system administration.
According to John Yeo, Trustwave’s European director, organizations that are being breached are typically not diligent enough in determining whether the third parties they are looking to work with will treat data security as seriously as they would themselves.
“Organizations are too quick to fight up the cost savings of outsourcing, but don’t really have an appreciation of what security risks that may introduce. The third-party evaluation process tends to be focused on costs and service level agreements (SLAs), without security being a real consideration.”
While outsourcing cybersecurity shouldn’t be viewed as inherently bad, these types of breaches do highlight one key perk of having your own team in-house: control.
With cybersecurity experts on staff, management maintains control of who works directly within their business network, and what types of information they have access to. They can monitor what their cybersecurity experts are doing and ensure they embrace the organizational culture.
In-house teams can also be informed of confidential business initiatives, and develop a deep understanding of the organization they work for. Not only do they know network hardware and software, but they know faces, names, and day-to-day activities.
In the same way that the best data backup system has multiple copies on different media, many businesses choose both in-house team members, and to outsource cybersecurity experts. From a cost perspective, it means they can have a smaller in-house team with the ability to scale in response to a cybersecurity incident.
While the ideal route will depend on the nature of your organization, any organization with more than a few hundred staff members and no in-house cybersecurity specialist may already be overlooking potential threats internally.
How to hire a cybersecurity specialist with confidence
The “State of Cybersecurity 2022” report from ISACA stated that 62% of organizations feel they are understaffed in terms of cybersecurity professionals. Adding further insult to injury, the study found that 60% of organizations have trouble holding onto qualified cybersecurity staff.
That same survey reported the primary reason cybersecurity staff leave is that they are recruited by other companies. According to the survey, other top reasons employees leave are high work stress levels and lack of management support.
Fundamentally, recruitment for cybersecurity needs to change, and these industry professionals are acutely aware of just how in demand their skills are. If your company is able to offer flexibility, realistic workloads, and a preview of what a candidate can expect at your organization, then you’re already one step ahead of the competition – but how do you achieve these benchmarks?
The key to hiring a cybersecurity specialist with confidence is job simulations. The experience and skill of a cybersecurity professional aren’t metrics that can be measured via a standard interview — and yet, countless companies continue to use impractical and outdated recruitment methods to attract this type of talent.
Instead of relying on resumes, degrees, or even interviews, a job simulation places a candidate in a network simulation to validate and verify their cybersecurity skills. In addition to the basics, hiring managers are also able to customize the simulation based on the type of work the cybersecurity specialist is expected to encounter on the job.
When the results of the job simulation are finalized, companies can expect to get a good idea not only of the applicant’s technical knowledge but their ability to manage stakeholders and work across departments.
For the candidate, a job simulation also provides a preview of what type of work they’re expected to encounter while working for the company, which can be revolutionary for reducing attrition – which is often caused by the work being different than expected.
As a company, Vervoe aspires to simulate the tasks of a role as close to reality as technology allows. Job simulations, such as our new cybersecurity simulations, do exactly that — simulating tasks exactly as candidates will experience them on the job, to give hirers an in-context view of how they’ll perform.
As the recruitment tool of the future, job simulations are rapidly becoming essential for identifying ideal candidates for highly skilled roles, particularly for cybersecurity.

Meet the experts on cybersecurity recruitment
Vervoe is an end-to-end AI-powered solution that is proudly revolutionizing the hiring process through skills testing, job simulations, and machine learning recruitment. By empowering businesses to create tailored assessments designed to suit the specific requirements of a role, Vervoe predicts performance using job simulations that showcase the talent of every candidate.
By assessing an applicant’s ability to perform the role through a skills assessment, our job simulations focus on the work — and not the person. To see people do the job before they get the job, book a demo today and let our experienced team run you through Vervoe’s full range of ready-made and tailored solutions.