When you think of a “hacker,” you probably unconsciously envision a mysterious hooded man, wearing blacked-out sunglasses, surrounded by illuminated screens filled with code, in a dark room, right? Contrary to popular belief, there’s a lot more to the world of cyber hacking than what we see on the screens.
From stealing, changing, and destroying information to protecting organizations’ digital space, there are various levels of hacking — good and bad — and many shades in between. Whether you’re considering a career in cybersecurity, or are an organization wanting to learn more about how to safeguard your business from the unfortunate prevalence of data breaches, here’s everything you need to know about good and bad hacking.
How prominent is hacking — and what is its impact?
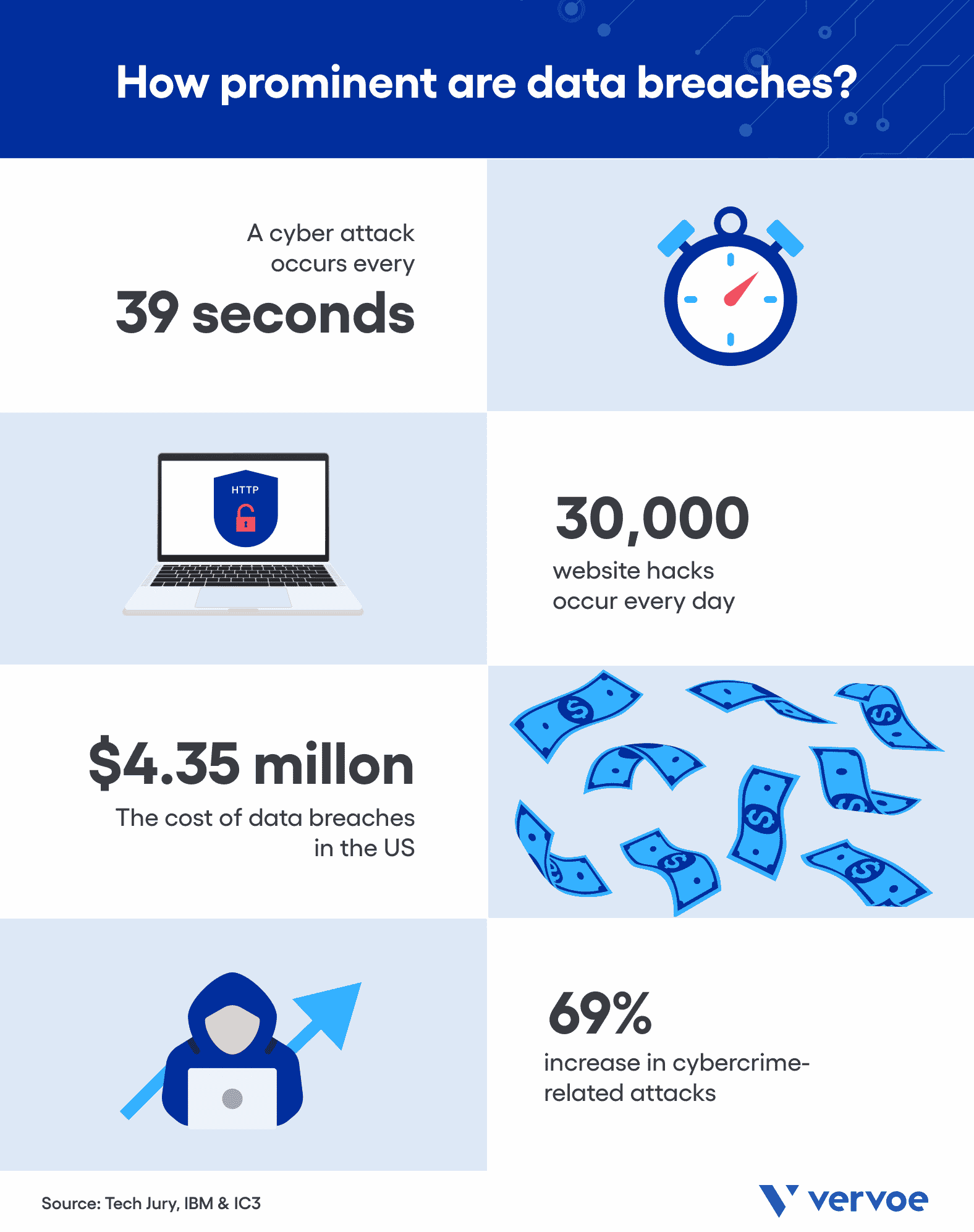
Cybersecurity is a global issue and a growing one too. According to Tech Jury, a cyber attack occurs every 39 seconds. Consider the following statistics when grasping the severity and impact of hacking:
- Thirty thousand website hacks occur every day, according to Tech Jury.
- Ransomware attacks are increasing by 400% year on year, according to IT Chronicles.
- More than 25,000 malicious applications are detected daily and subsequently blocked.
- 70% of all global data breaches are due to financial motives. Annually, the cost of cybercrime is $1.5 trillion globally.
- In 2020, healthcare data breaches in the US increased by 25% from the previous year.
- Since 2019, the FBI has seen a 69% increase in cybercrime-related attacks.
- According to IBM, the cost of data breaches in the United States has hit a new record, averaging a total cost of $4.35 million in 2022 — a 12.7% increase from 2020.
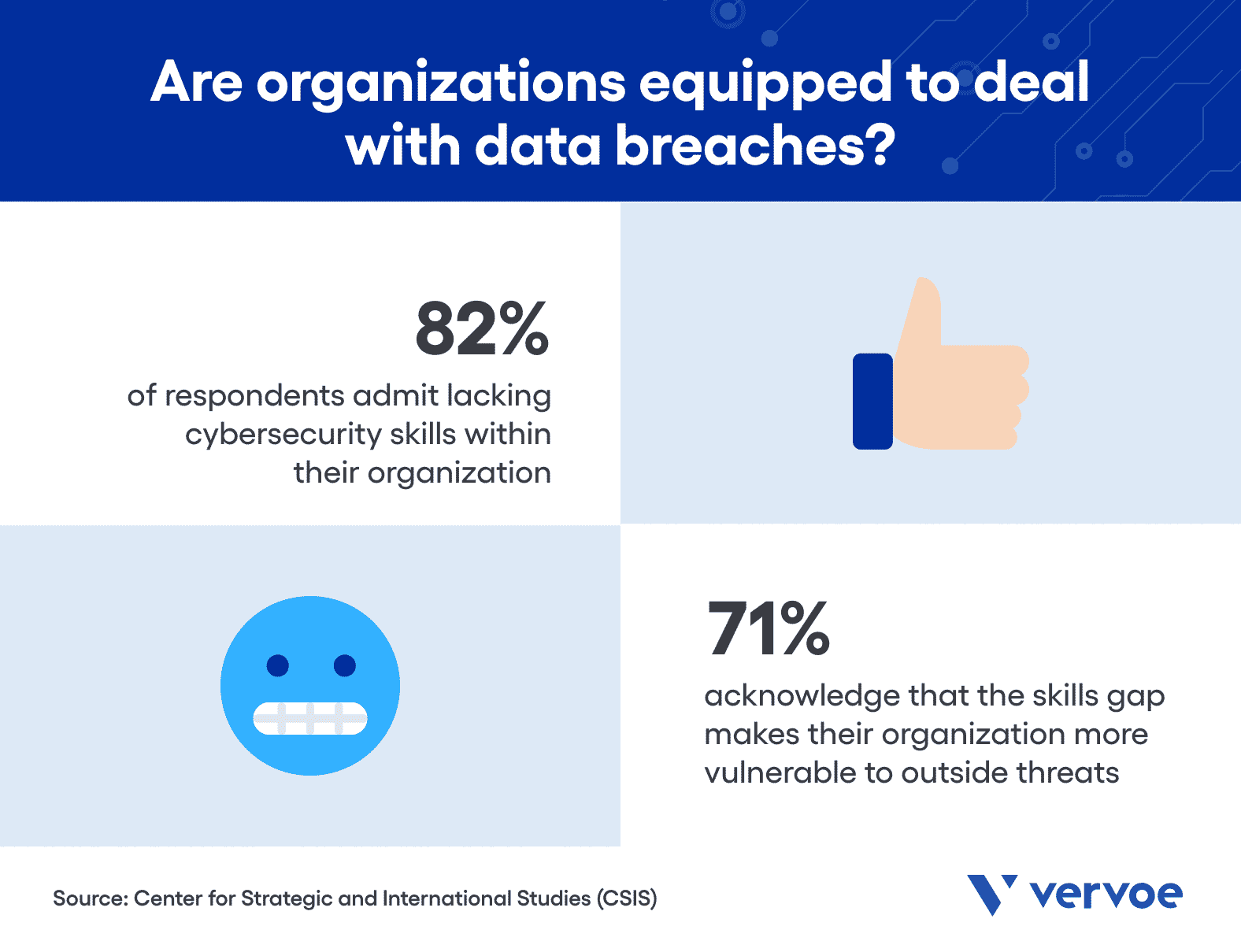
The growing prevalence of data breaches is undeniable. And unfortunately, their impact is felt in organizations — large and small — in every corner of the world. According to a 2016 Center for Strategic and International Studies (CSIS) study, 82% of respondents admit lacking cybersecurity skills within their organization, and 71% acknowledge that the skills gap makes their organization more vulnerable to outside threats.
Another 2021-22 study conducted by IBM, which interviewed over 3,600 individuals from organizations impacted by data breaches, drew the following conclusions:
- 45% of data breaches were cloud-based.
- 83% of organizations have experienced more than one data breach.
- 60% of data breaches forced organizations to increase their prices on a consumer level.
- On average, it took 277 days to identify and contain a data breach.
What is “hacking”?
According to the Economic Times, hacking refers to the action of gaining control of a computer system or a private network inside a computer.
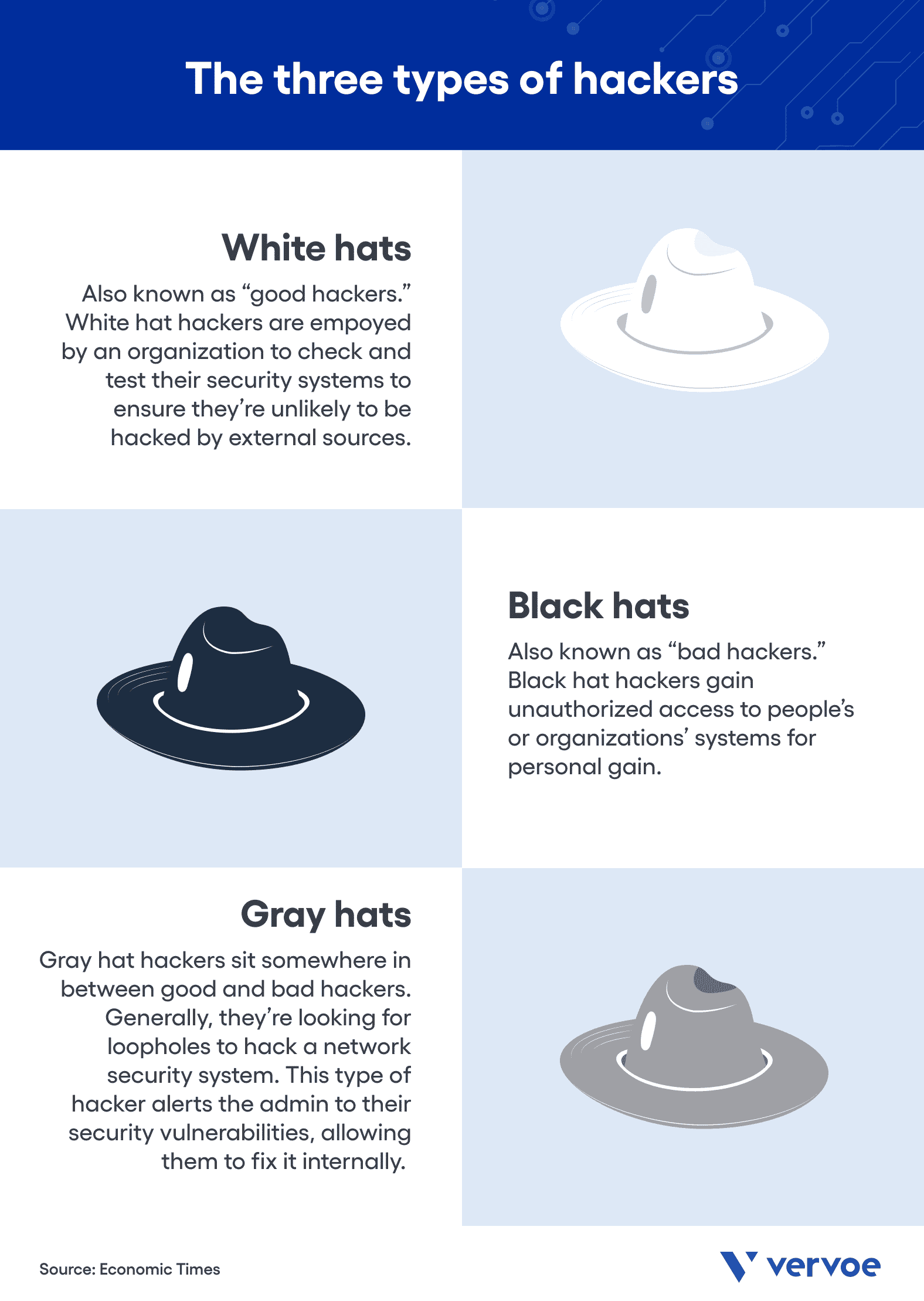
Yet, to truly understand how hacking works, it’s important first to understand the varying types of hackers and the intention behind their skills — good and bad. When talking about hackers, they’re often categorized into three primary groups:
- White hats — An organization often employs these hackers to check and test their security systems to ensure they’re unlikely to be hacked by external sources.
- Black hats — These are the hackers you watch in movies. They gain unauthorized access to people’s or organizations’ systems for personal gain.
- Gray hats — This group is known as the curious hackers. Generally, they’re looking for loopholes to hack a network security system. However, unlike black hats, they aren’t operating for personal gain. This type of hacker alerts the admin (i.e., organization) to the weakness, allowing them to fix it internally.
Black, gray and white hats: the different types of hackers explained
White hat hackers
What are white hat hackers?
White hat hackers, also known as ethical hackers or good hackers, engage in a legal form of hacking whereby they’re employed by an organization or business to identify security flaws and make recommendations for improvements. Unlike black hat hackers, their intentions focus on strengthening the security network to avoid potential threats.
What do white hat hackers do?
Essentially, their job is to identify system vulnerabilities to prevent security breaches. They achieve this by trying to mimic what a bad hacker (black hat) would do. Often, this includes the following process:
- Research — They will try identifying vulnerability points in the program or technology. This can be done manually or through an automated process.
- Document — Seek to understand how the vulnerability can be exploited.
- Discuss — Often, they will provide a detailed analysis of the pain points and solutions.
It’s important to note, for hacking to be considered ethical and legal, the hacker needs permission from the system owner to gain access to their network and identify potential weak points.
How do white hat hackers work?
There are several skills and tests that white hat hackers deploy to test the strength of a security system. As they’re trying to mimic what a black hat hacker would do, these may include one or more of the following, according to Kaspersky:
- Social engineering — Also known as “people hacking,” this refers to tricking and manipulating victims into doing something they shouldn’t to test the weaknesses of an organization’s human defenses. This might include sharing login credentials or making a wire transfer.
- Penetration testing — This involves identifying potential weaknesses in a company’s security defenses and rectifying the vulnerabilities.
- Research — This refers to researching a company to identify weaknesses within the IT and physical infrastructure. Hackers seek ways to bypass security controls without interfering or breaking anything legally.
- Programming — Good hackers create honeypots, aimed at luring in bad hackers to distract them or gather valuable information on them. Good hackers will sacrifice the computer system to help attract bad hackers.
While both good and bad hackers have the same skill set, they differ in their intent. As such, while they both aim to bypass a system’s defenses, an ethical hacker has little interest in taking advantage of the vulnerabilities for personal gain. Instead, they aim to help identify and correct said weaknesses.
Gray hat hackers
What are gray hat hackers?
When it comes to cybersecurity, it isn’t black and white. As the name suggests, gray hat hackers
sit somewhere in between good and bad hackers. Many gray hat hackers choose to hack systems and networks as a hobby or to identify vulnerabilities and alert the owner to potential security risks. Unlike black hat hackers, there is often little interest in personal gain, although the line can easily be crossed.
What do gray hat hackers do?
While gray hat hackers’ intentions are generally good and are aimed at providing valuable information to companies, it’s important to note that their actions are technically illegal, and many white hat hackers consider their methods unethical. Likewise, it’s not uncommon for gray hat hackers to switch to black hat hackers should an opportunity arise.
Motivation is the main difference between a black hat hacker and a gray hat hacker. While black hat hackers are self-serving and looking for personal gain, gray hat hackers’ motives are intriguing. While motivation will vary from person to person, many categorize their intentions into one or more of the following groups:
- They feel a societal duty to make the internet safer for individuals and organizations.
- Their curiosity takes over, and they want the challenge of hacking into a high-profile system.
- They want to showcase their skill set or gain publicity.
How do gray hat hackers work?
Gray hat hackers will use one or a combination of the methods used by white hat hackers to identify issues and make recommendations. Often they’ll find weaknesses and alert the organization to the issues.
However, depending on how ethical the gray hat hacker is, this isn’t always the case. Walking a fine line between being a silent superhero and putting businesses at greater risk, there are many shades of gray when it comes to gray hat hackers. This includes:
- Recommend fixes — The gray hat hacker may alert the organization to the vulnerabilities and provide a list of recommendations to fix the problem. In some instances, they may offer their services for a small fee. Although, this is less common now as businesses are more likely to prosecute hackers for their illegal activity.
- Bug bounty programs — Many organizations are aware of the risks hackers pose to their overall security. As such, many larger companies use bug bounty programs, whereby they pay a bounty for any vulnerabilities detected by a hacker. This lowers the risk of hackers exploiting their weaknesses or publicly alerting other hackers to the issues.
- Public announcement — In certain situations, some gray hat hackers may publicly post the organization’s weaknesses, opening them up to potential cyberattacks by various black hat hackers. While their intent may not be malicious, it puts the business at greater risk of attack by those who are unethical in their practices.
Black hat hackers
What are black hat hackers?
Black hat hackers, also known as bad hackers, engage in illegal hacking motivated by personal gain — from financial and political to revenge. Black hat hackers will generally work alone or for organized crime units.
What do black hat hackers do?
Simply put, black hat hackers, or bad hackers, break into computer security networks without authorization to inflict damage. The extent of black hat hacking is varied — from releasing malware to destroy files, holding systems hostage, thieving passwords, and holding onto personal information, such as credit card numbers. Given the legal ramifications of their work, black hat hackers work extremely hard to remain anonymous — adding to the mysterious nature of hacking.
How do black hat hackers work?
Cyberattacks range in severity and can present in many different forms. According to Dataprot, here are a few of the most common forms of hacking conducted by black hat hackers:
- Phishing — This involves bad hackers sending out emails posing as companies the victim is connected with (i.e., their banking institution). Generally, victims are enticed to click on a malicious link that collects sensitive information, such as login details.
- Bait and switch attack — This involves hackers purchasing advertising space online and infecting people’s devices when clicked on.
- Ransomware — Ransomware blocks access to a person’s files and system. Hackers generally request money in exchange for unblocking the system.
- Keyloggers — A keylogger is a type of software that records each key a person types. Essentially, this gives hackers access to sensitive information, such as passwords.
Good vs bad hacking: a side-by-side comparison
While good and bad hackers appear to sit at opposite ends of the spectrum, the reality is they’re similar in nature. While their motives drastically differ, their skill set and hacking methodology remain largely the same. Let’s take a closer look at a side-by-side comparison created by Knowledge Hut:
| Boundaries | Good hacking | Bad hacking |
| Motive | A good hacker would work with an organization or business to protect their data. This includes researching and detecting security vulnerabilities, providing recommendations and repairing flaws, and implementing data protection policies. | A bad hacker gains unauthorized access to an organization or business’ system for personal gain — financial, political, revenge, or for enjoyment. |
| Legalty | This form of hacking is legal as the organization or business has hired or contracted the hacker and given them authorized access to their network and technology. This is one of the most in-demand and highest-paying fields currently. | This form of hacking is illegal as the hacker is trying to gain unauthorized access to a system’s network to cause malice. There are serious consequences if found guilty. |
| Tools | Ethical hackers use the same tools as bad hackers to identify vulnerabilities and potential weaknesses | Bad hackers use the same tools as ethical hackers to exploit said vulnerabilities for personal gain. |
| Training | Ethical hackers often have the same training and skill set as bad hackers. Good hackers can choose to gain additional certification to prove their intention, such as the Certified Ethical Hacker (CEH) certification. | Bad hackers often have the same training and skill set as ethical hackers. |
A career in ethical hacking and cybersecurity — what skills are required?
With the demand for quality cybersecurity professionals skyrocketing, businesses and organizations alike recognize that quality talent comes from many walks of life and varying career pathways. What does this mean? There isn’t a one-size-fits-all approach to entering the cybersecurity workforce. While some people will wind up in cybersecurity-related careers through specific college degrees, others will arrive through self-teaching and transferable skills.
Let’s take a closer look at what skills are required to be an ethical hacker:
| Ethical hacker hard skills: | Ethical hacker soft skills: |
| Expertise in programming languages (i.e., Python, SQL, C++, Java, C, Ruby, JavaScript, Perl, PHP, etc.) | Communication |
| Proficiency in operating systems | Problem-solving |
| Thorough working knowledge of networking | Critical thinking |
| Proficient in information security principles | Analytical |
| Knowledge of database management systems | Organizational |
| Knowledge of platforms i.e., Windows, Linux, Unix, etc. | Creativity |
| Knowledge of search engines and servers | |
| Troubleshooting |
Final thoughts
It’s no secret that we live in a period defined by technology, software, and data — and predictions suggest this is on an upward trend.
With greater reliance on technology comes greater pressure for organizations to find quality, sustainable, and efficient methods to safeguard their organization’s online presence.
Enter: ethical hackers.
From researching and detecting security weaknesses to providing recommendations and fixes for said vulnerabilities, ethical hackers are paving the way for the future of cybersecurity. And organizations have a duty to their technology to educate themselves on the difference between good and bad hackers and their many synonyms.
At Vervoe, we’re committed to ensuring every candidate you hire is the best person for the job. To learn more about how our pre-employment assessments and skills validation platform can help you hire leading tech talent, request a demo today.