Cybersecurity Best Practices for Recruiters
Recruiting Daily
JULY 24, 2023
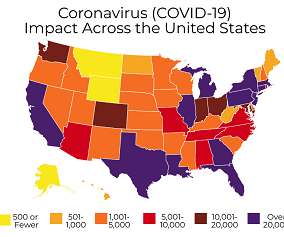
Recruiters are also vulnerable to social engineering tactics like phishing and spoofing scams. Depending on what type of data you’re collecting, you may even be legally required to make a disclosure to your candidates and put certain security measures in place. Some hackers will use brute force attacks to crack passwords as well.





















Let's personalize your content